Investigation bad people might involve bitcoin, the blockchain technology is very popular among criminals, as it is easy to use and „untraceable“ [1]. E.g. in most ransomware cases like „Ryuk“ [2] the company Crowdstrike has listed several bitcoin wallets, that they attribute to the threat actor.
How can that information help your investigation / your intelligence gathering? IN certain ways, you could track your own wallets for transactions to these wallets. Another aspect, that this blogpost will cover on is the timeline aspect of it.
As bitcoin transactions make use of the blockchain, who is public by design, it is possible to:
- tell, how many bitcoins a certain wallet currently holds
- see transactions from the past
The second aspect is what I want to focus on, because if we have a look at the transactions, we might be able to identify the point in time a certain group was active and enhance our other DFIR activities enriched with that information. The transaction log is like your journal of your bank account, it tells basically who is transferring money to a wallet and where the bitcoins are transferred to.
In the example above, the bitcoin wallets we are interested in are (Source Crowdstrike Blog post):
| BTC Address | Total Received | No Received | Total Value (USD) |
| 12vsQry1XrPjPCaH8gWzDJeYT7dhTmpcjL | 55.00 | 3 | $221,685.46 |
| 1Kx9TT76PHwk8sw7Ur6PsMWyEtaogX7wWY | 182.99 | 10 | $734,601.91 |
| 1FtQnqvjxEK5GJD9PthHM4MtdmkAeTeoRt | 48.250 | 4 | $188,974.93 |
| 14aJo5L9PTZhv8XX6qRPncbTXecb8Qohqb | 25.00 | 2 | $113,342.70 |
| 1E4fQqzCvS8wgqy5T7n1DW8JMNMaUbeFAS | 0.001 | 1 | $6.47 |
| 1GXgngwDMSJZ1Vahmf6iexKVePPXsxGS6H | 30.00 | 3 | $132,654.91 |
| 1Cyh35KqhhDewmXy63yp9ZMqBnAWe4oJRr | 0.00 | 0 | $0.00 |
| 15LsUgfnuGc1PsHJPcfLQJEnHm2FnGAgYC | 0.00 | 0 | $0.00 |
| 1CbP3cgi1Bcjuz6g2Fwvk4tVhqohqAVpDQ | 13.00 | 2 | $82,917.49 |
| 1Jq3WwsaPA7LXwRNYsfySsd8aojdmkFnW | 35.00 | 1 | $221,979.83 |
| 129L4gRSYgVJTRCgbPDtvYPabnk2QnY9sq | 0.00 | 0 | $0.00 |
| 1ET85GTps8eFbgF1MvVhFVZQeNp2a6LeGw | 3.325 | 1 | $12,661.74 |
| 1FRNVupsCyTjUvF36GxHZrvLaPtY6hgkTm | 38.99 | 3 | $246,893.95 |
| 1CW4kTqeoedinSmZiPYH7kvn4qP3mDJQVa | 24.077 | 2 | $152,727.13 |
| 13rTF3AYsf8xEdafUMT5W1E5Ab2aqPhkPi | 0.00 | 0 | $0.00 |
| 17zTcgKhF8XkWvkD4Y1N8634Qw37KwYkZT | 0.00 | 0 | $0.00 |
| 14dpmsn9rmdcS4dKD4GeqY2dYY6pwu4nVV | 0.00 | 0 | $0.00 |
| 17v2cu8RDXhAxufQ1YKiauBq6GGAZzfnFw | 0.00 | 0 | $0.00 |
| 1KUbXkjDZL6HC3Er34HwJiQUAE9H81Wcsr | 10.00 | 1 | $63,358.27 |
| 12UbZzhJrdDvdyv9NdCox1Zj1FAQ5onwx3 | 0.00 | 0 | $0.00 |
| 1NMgARKzfaDExDSEsNijeT3QWbvTF7FXxS | 0.00 | 0 | $0.00 |
| 19AE1YN6Jo8ognKdJQ3xeQQL1mSZyX16op | 25.00 | 1 | $164,774.21 |
| 1L9fYHJJxeLMD2yyhh1cMFU2EWF5ihgAmJ | 40.035 | 4 | $259,478.16 |
| 18eu6KrFgzv8yTMVvKJkRM3YBAyHLonk5G | 30.00 | 1 | $198,651.35 |
| 1C8n86EEttnDjNKM9Tjm7QNVgwGBncQhDs | 30.0082 | 2 | $194,113.76 |
| 12N7W9ycLhuck9Q2wT8E6BaN6XzZ4DMLau | 0.00 | 0 | $0.00 |
| 162DVnddxsbXeVgdCy66RxEPADPETBGVBR | 0.00 | 0 | $0.00 |
| 1ChnbV4Rt7nsb5acw5YfYyvBFDj1RXcVQu | 28.00 | 2 | $175,177.98 |
| 1K6MBjz79QqfLBN7XBnwxCJb8DYUmmDWAt | 1.7 | 2 | $12,455.95 |
| 1EoyVz2tbGXWL1sLZuCnSX72eR7Ju6qohH | 0.00 | 0 | $0.00 |
| 1NQ42zc51stA4WAVkUK8uqFAjo1DbWv4Kz | 0.00 | 0 | $0.00 |
| 15FC73BdkpDMUWmxo7e7gtLRtM8gQgXyb4 | 0.00 | 0 | $0.00 |
| 14hVKm7Ft2rxDBFTNkkRC3kGstMGp2A4hk | 10.00 | 2 | $64,990.62 |
| 1CN2iQbBikFK9jM34Nb3WLx5DCenQLnbXp | 15.00 | 1 | $92,934.80 |
| 1LKULheYnNtJXgQNWMo24MeLrBBCouECH7 | 0.00 | 0 | $0.00 |
| 15RLWdVnY5n1n7mTvU1zjg67wt86dhYqNj | 50.41 | 3 | $326,477.83 |
| 1KURvApbe1yC7qYxkkkvtdZ7hrNjdp18sQ | 0.00 | 0 | $0.00 |
| 1NuMXQMUxCngJ7MNQ276KdaXQgGjpjFPhK | 10 | 1 | $41,034.54 |
Source of transaction information
There is a whole bunch of public webpages who give transaction history for a given wallet, but as it should be an automated step, the goal is to have a page with an API, after some searching I found: https://chain.so/api .
Making the call
Doing the API call to get transaction information is pretty simple:
GET /api/v2/address/{NETWORK}/{ADDRESS}
That will give you the following information
{
"status": "success",
"data": {
"network": "DOGE",
"address": "DM7Yo7YqPtgMsGgphX9RAZFXFhu6Kd6JTT",
"balance": "31.03885339",
"received_value": "25828731.93733507",
"pending_value": "0.0",
"total_txs": 225,
"txs": [ ... ]
}Which is exactly what we need, with some Python JSON parsing, it is easy to get the info we want – the code I am using is available on https://github.com/deralexxx/osint_to_timesketch
After that we have an CSV with the date, the transaction happened, the raw information from the API and some meta data, enough to bake into a timeline.
Automation
The script is already made to output CSV files ready for importing them into Timesketch, as I found it to be the ideal tool to work with data points related to timestamps. Importing the CSV is straight forward and explained in the official documentation page [3].
The timeline csv looks like the following:

Making it pretty
Importing it into Timesketch, the timeline looks very nice:
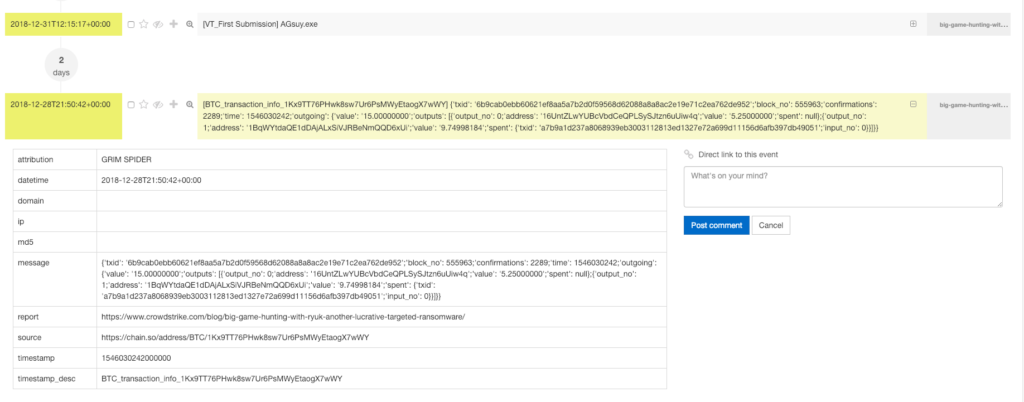
Added Value
Now what is the added value for investigations? The above is another layer of data points /evidence. It can be used to weight limit findings in your organisation, e.g. you assume you are hit by a phishing campaign, if your phishing campaign was seen a lot earlier or a lot later than the transactions above display, it is unlikely you are hit by the same campaign. It can also be used to make a case against individuals if enriched by host forensics – your imagination is the limit.
End
I hope the article is helpful and the scripts can be used, let me know via comments within the blog, issues on github or twitter messages https://twitter.com/alexanderjaeger if you have any questions, improvements.
Thx for reading
Further reading / references
- [1] http://www.sciencemag.org/news/2016/03/why-criminals-cant-hide-behind-bitcoin
- [2] https://www.crowdstrike.com/blog/big-game-hunting-with-ryuk-another-lucrative-targeted-ransomware/
- [3] https://github.com/google/timesketch/blob/master/docs/CreateTimelineFromJSONorCSV.md